Last year, Google was criticised for accessing users’ inbox to show them relevant ads. In the time that followed, the search giant stopped its practices, but the ability for third-party apps to look into people’s Gmail inbox remained intact.
Recent reports have suggested that not just the computers and apps, even third-party developers are able to read people’s emails. And the practice doesn’t happen without the explicit consent of the users which doesn’t explicitly mention that the data accessed would be viewed by human eyes.
Google has also clarified that Gmail access to third party apps isn’t given without them being subjected to a thorough vetting process.
Anyway, there may or may not be some evil mind trying to access your Gmail. But taking an extra step towards your privacy and security is a must. You can find out what apps can look into your Gmail inbox.
How to check and disable apps from accessing your Gmail account?
Every setting associated to your Google account can be managed by visiting the My Account page. There you can find what third-party apps are connected to your Google account and what kind of data they’ve access to.
Follow the steps mentioned below:
- Sign-in to your Google account and go to the My Account page.
- Under Sign-in & security, click on Apps with account access.
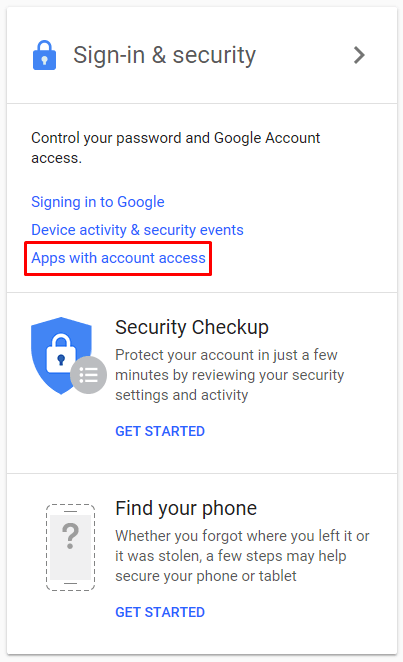
- On the page, click on Manage Apps.
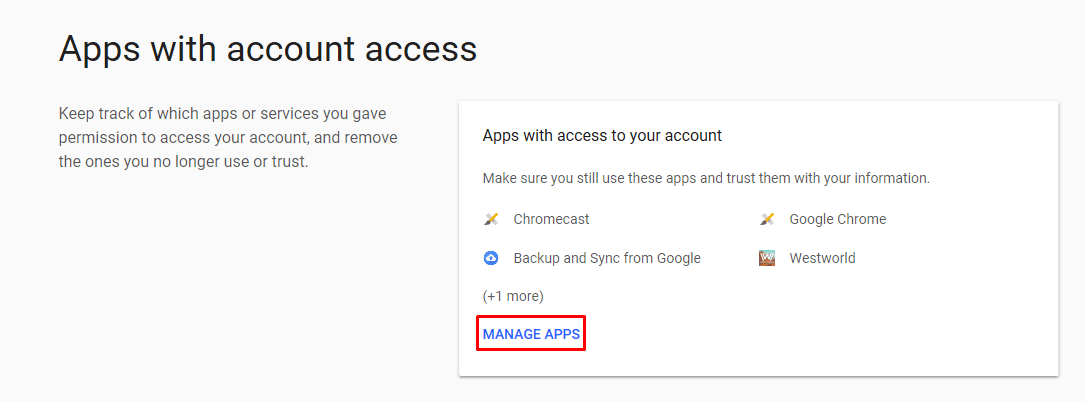
- Now, a list of all the apps (Google and non-Google) having access to your account is displayed. The level of permissions they’ve have is also shown.
- You can click on any app name to expand it and view what it can do with the permissions and when it was granted.
- Next, click on Remove Access to revoke all the permissions given to the particular app.
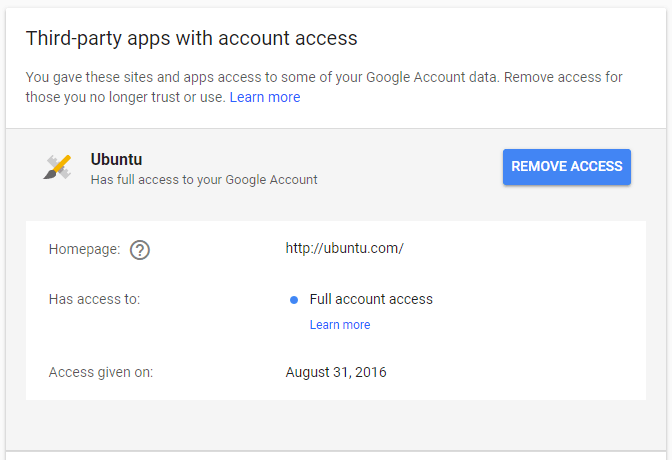
So, this way you can disable Gmail access for third-party apps. But you should also keep in mind that pulling the permissions may affect the normal operation of some apps that require Google services to work. For instance, if you’re using a Calendar app with your Google account, it should have read and write permission to edit your Google calendar.
“Has full access to your Google account” – What does it mean?
Out of the many apps connected to your account, some can only read basic information or access a couple of services. On the other hand, some have complete access to your Google account.
With full access, it can view and modify almost all of the information in your Google account. Still, there are few essential things it can’t do. For instance, it can’t change your password, delete your Google account, or make Google Pay transactions.
Mostly Google-made apps have full access to your account, but it could be given to third-party apps as well. However, if you don’t trust or recognize an app with full account access, you should remove access immediately.
YOU MAY ALSO LIKE:

Comments
Post a Comment